Here is the some popular Linux Distros for Penetration Testing and Ethical
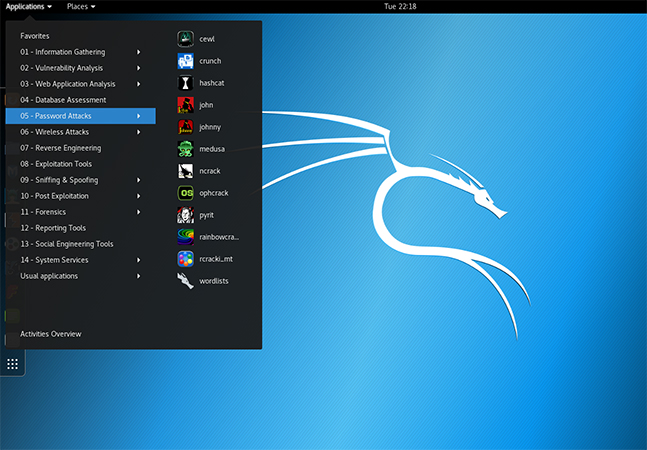
- Kali Linux:
Kali Linux is an open source project that is maintained and funded by Offensive Security, a provider of world-class information security training and
penetration testing services.
- BackBox
BackBox is an penetration test and security evaluation oriented Ubuntu-based Linux distribution providing a network and informatic frameworks analysis toolkit.

- Parrot Security OS:
It is likewise a Debian-based operating system that is created by Frozenbox’s group. Parrot security is a cloud-accommodating operating system designed for ethical hacking, pen testing, computer forensics, cryptography, etc.
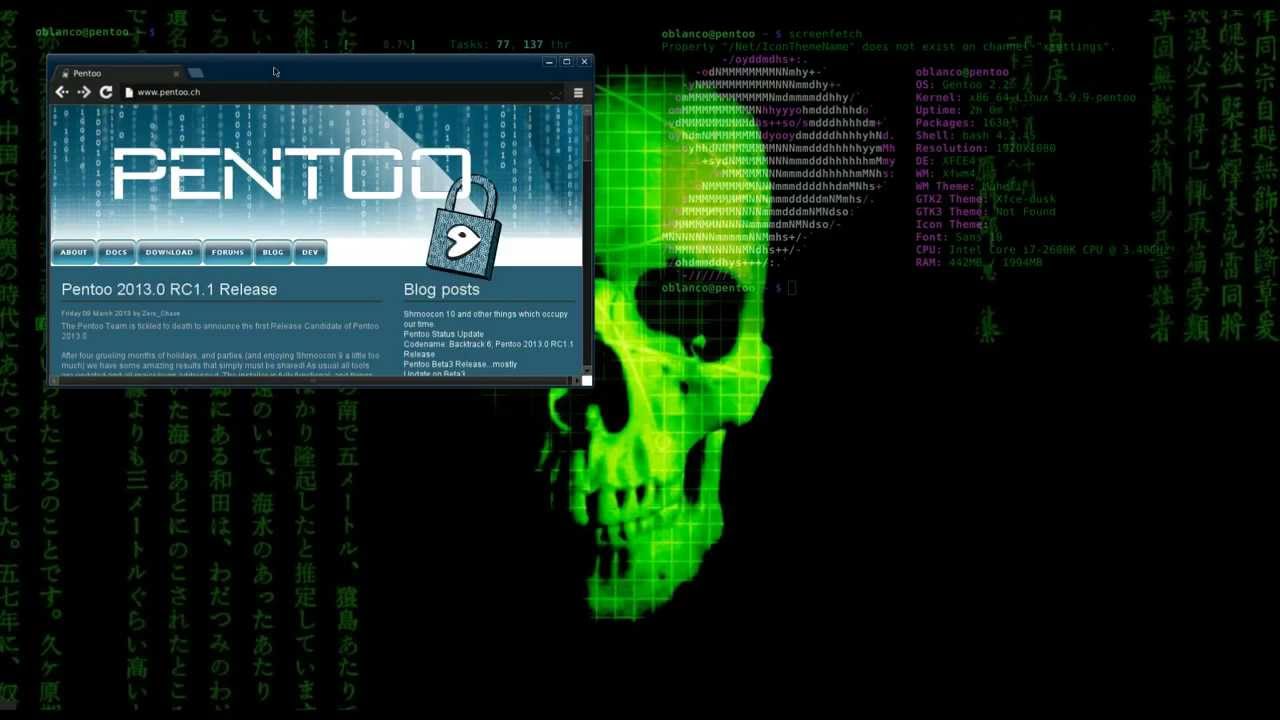
- Pentoo Linux:
Pentoo is a pen testing focused operating system based on Gentoo Linux. It can be used on top of an existing Gentoo Linux installation.
- Samurai Web Testing Framework:
Samurai Web Testing Framework is essentially a live Linux environment that comes pre-configured to work as a web penetration testing platform.
- Caine:
Security focused distro “Caine” is an Ubuntu-based operating system that is available as a live disk. It stands for Computer Aided Investigation Environment.

- Network Security Toolkit (NST):
Fedora-based Linux distro “Network Security Toolkit” runs on 32 and 64-bit platforms. This bootable live CD was created to give you a right to use the best open source network security applications for pen testing purposes.
- Bugtraq:
Bugtraq is famous for its electronic mailing list that is purely dedicated to computer security. It is available in Debian, Ubuntu, and OpenSUSE.
- BlackArch Linux:
BlackArch Linux is an absolute Linux distribution for security researchers and ethical hackers. It is derived from Arch Linux, and one can also install the BlackArch Linux components on top of it.
- DEFT Linux:
The open source Linux distribution “DEFT” stands for Digital Evidence and Forensic Toolkit. DEFT is based on Ubuntu and built around the DART (Digital Advanced Response Toolkit) software.
For more details about Linux Distro for Penetration Testing